To protect the security of systems, Data, APPs and Websites
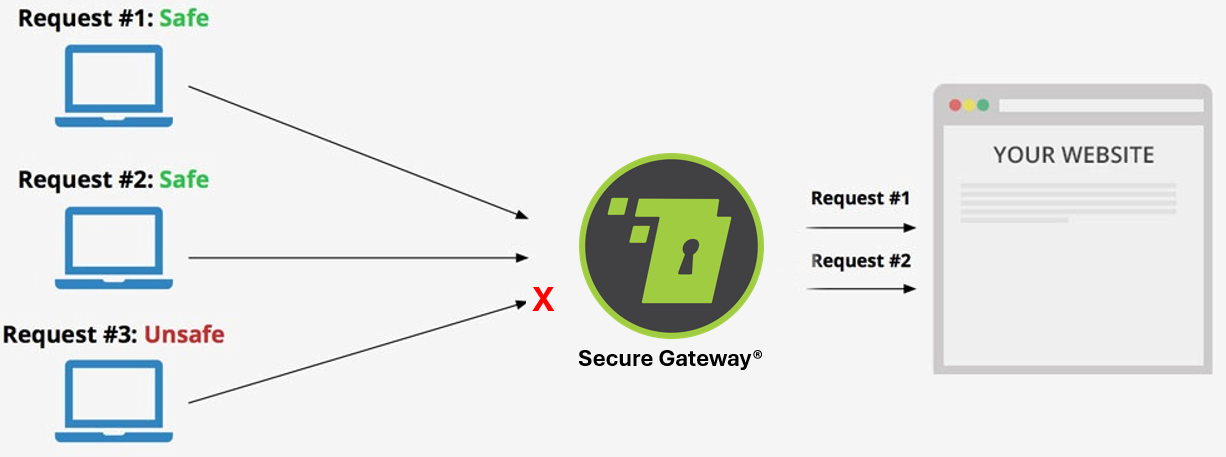
Secure Gateway is a state-of-the-art technology used to protect information and data security using Network Traffic Analysis (NTA) where all incoming requests are controlled by passing through central servers called Secure Gateway. These requests are then analyzed and transferred by the Secure Gateway servers to the real host servers of the e-system (your website). As a result of the requests going through the Secure Gateway servers, the requests will be analyzed by the NTA technology, filtered, and the requests will be partitioned into real requests and phishing requests. The Secure Gateway servers isolates phishing requests. Only real requests are passed to the host servers of the e-system. At that point, no visitor can find out where the real hosting servers are and cannot access the data they contain unless they pass through Secure Gateway servers; the real servers only receive the requests from Secure Gateway servers rather than directly from the users. Secure Gateway technology is a worldwide trademark registered with US Registration No: 5899344 and US Registration No: 6079175 and registered as a global patent using NTA technology known as Network Traffic Analysis with U.S Patent Registration No: 10498760 and U.S Patent Registration No: 10630721.
Patents for Secure Gateway technologies have been approved and published on Google's patent website https://patents.google.com on the link https://patents.google.com/patent/US10498760B1 and link https://patents.google.com/patent/US10630721B1.
1 - The mechanism of passing requests across Gateway servers.
Secure Gateway servers analyze the request that passes to the website by reading the code passing through the Secure Gateway where the the request is analyzed. If the target of the request is to hack or attempt to hack the data, the Secure Gateway automatically removes those requests. This provides a security layer for information on the website.
2 - Protection from "DDoS Attack" to ensure the continuity of the website work around the clock
The Distributed Denial of Service (DDoS) attack is one of the most dangerous types of attack on an electronic system and considered to be the easiest attack that can be performed because there are many free and paid for programs that do this. The Secure Gateway servers provide full protection for this type of attacks because the attack (hack) must travel through the Secure Gateway servers. When the hacker sends hundreds or thousands of requests per second or minute, these requests will not reach the site or the actual system, but reach the Secure Gateway servers where the Secure Gateway servers denies the malicous requests and only allows the correct requests. Without this protection, the e-system and website services will become slow and will cease to function. Ddos Attack protection will preserve the health of your website.
3- Check the files uploaded to the site and analyzing it using the technique of "Spider Security"
One of the first steps taken by the hacker to control the system data and website is to upload a virus file to control the website. In this kind of attack, even if the passwords are changed, he/she will stay in control. The hacker uploads the virus through a page on your website that is designed for the website visitor to upload files. Even if the hacker is able to upload viruses by changing the extension of the virus file from the executable extensions file formats to the extensions allowed by the site (for example - pdf, doc, jpg), the Secure Gates blocks this attack. Here comes the function of the Gateway Servers where we use advanced technology called Spider Security and through Gateway servers we receive the file instead of the original hosting server. The Secure Gateway analyzes the file programmatically by converting it back to the binary format. After examining the file we will send it to the real hosting server only if it is a normal file that do will not lead to any damage to the hosted website. If the file is a virus we delete it and prevent it access to the real server.
For example, the hacker sends a virus in the form of a fake picture attachment. Here comes the role of the Secure Gateway. By reading the file with Binary technique, the file will be exposed and isolated before it reaches the real server of the site.
4- Protection from hacking programs and system analysis programs or website
When using Secure Gateway technology, this technology helps prevent and stop all programs that hope to penetrate the site or system. When accessing the system or website, the Gateway servers send requests to the user's account to make sure that they are using real browsers such as Firefox, Google Chrome or Internet Explorer. If the client replies does not use these browsers that likely means that the hacker has written a malicious program that is pretending to be a user. Through the Secure Gateway we can prevent this kind of attack. We use the latest technology to detect the type of program used by the visitor and in the following ways:
A) Secure Gateway servers tracks the movement of the visitor within the site and if we notice that the visitor visits the pages of the site more than the normal limit, for example, 30 pages per minute, this means that it is not a real visitor. The visitor is in reality a malicious program. Here we track every move by the “user.†The servers of the Secure Gateway automatically send a request to this user's electronic device to confirm the type of program that he/she using and if we detect that he/she uses a phantom or malignant program, we remove it directly.
B) Secure Gateway servers record and calculate the pages visited by the user according to mathematical calculations. On a regular time schedule, vulnerability detection programs scan all the files in your website in ascending or descending order, and scan the POST command and the GET command. This scan is especially important for websites that rely on the databases in their work, where the page name is fixed except for the last digit(s) which change and match the log number in the database. Here, the Secure Gateway servers expose the person who is trying to hack the site by using a Gap Detection Program.The Gap Detection program is a program which looks for vulnerabilities and protects against them. The Secure Gateway servers scan the website page in ascending and descending manner and when it exposes the attack will immediately remove the hacker from the system servers and the real website.
5- Protection against DNS shutdown
Gateway technology provides protection against DNS attacks. If the hacker tries to attack the DNS and is successful, the attack will completely stop the DNS lookups of the domain name. For example, DNS lookups to resolve “exmple.com†to the correct IP address for your website site will stop working completely. By using the Secure Gateway technology, the DNS attack is prevented, and the attack is transferred from the domain name of the site to the Gateway servers, which in turn will absorb and stop the attack and keep the system or website functioning naturally.
6. Provide WAP Firewall for data protection
WAP Firewall is considered one of the basic services that must be provided to protect the system or website from hacking because it prevents the hacker from creating Loops on the pages of the site, which leads the site to its maximum capacity of visitors access which is called Concurrent Connections and this attack causes the system or the website to stop working despite the fact that the server continues to work because the attack targets the internal system of the server and not the server itself. The use of Secure Gateway technology prevents the hacker from doing this because Gateway servers calculate the number of hits per page per person within a specified period. If this number is exceeded, the hacker will see a page that shows that he was prevented from entering due to his performing of illegal operations.
7 - Protection from URL Injection SQL Injection and XSS Injection
Once the site or system passes through the Secure Gateway servers, the technology examines and analyzes each request that passes through the servers, and whether the person is trying to perform illegal attacks intended to hack the system or website. If the attacker attempts more than 10 times, the Secure Gateway servers will prevent the person from accessing the site for 48 hours. Hacking by the Injection methods is a very common attack.
8 - Protection from Flood Attack and Bandwidth protection from consumption
One of the advantages of the Secure Secure Gateway technology is to protect the bandwidth used. Secure Gateway reduces the size of large data such as PDF files and compressed files (rar, zip iso) during transfer and thus will maintain the performance of your website. If it is the case that this technology is not available, the hacker may be able to consume all the bandwidth in a day or two and the site will stop working until the end of the month or you may have to purchase more bandwidth for the month. The hacker usually searches for the largest file sizes in the server and download it hundreds and thousands of times which cause all the allowed bandwidths to be consumed. The Secure Gateway technology can control the speed of transfer of these files and prevent attack in this way.
9 - Provide a service to hide the real location of servers hosting by hiding the IP
One of the advantages of Secure Gateway is to hide hosting servers and data centers of you website. The malicious hacker cannot access the real servers. In the case of this attack, if the hacker is able to get to the real server, he/she will be able to put the server on a "Black List." The reason for not being able to know the actual IP address is that the visitor will only see the Secure Gateway IP and does not know the real IP address of the server. This technology provides a very important security feature for maintaining the confidentiality and security of servers.
10- Informing the visitor that the system or website is encrypted with the Secure Gateway service
As soon as the system or the website is secured through the Secure Gateway servers, a visitor icon will appear indicating that the system or website is monitored and insured by Secure Gateway. This will give the visitor a safe indication that the site is secured and can be used safely without the fear of viruses or harmful files or the theft of his/her data.
11 - Detect the way the penetration is made
The Secure Secure Gateway advantage is that it can be applied to any site or electronic system of any kind, regardless of the type of language used in programming - whether the language used is asp, php, java etc. - and regardless of the type of data base (MySql, MSSQL, Oracle etc). Even if the programming script is weak and the site was hacked, through the technology of Gateway we can detect and identify the hacking method and find the name of the file through which the hacking process happened. In this way programmers working on the system will be able to repair and patch the vulnerability. Secure Gateway servers provide an audit trail so programmers can patch the site. Without the application of this technique the person will hack the system the real reason for the hacking will stay unknown which leads to repeated hacking on the same site.
12 - Log of all daily operations that occur on the Log File site
When the system or the website passes through the Secure Gateway servers, technical technology is available to record all operations and visits to and from the electronic system where it is possible to obtain a very accurate statistic about the number of requests entered or exited to and from the website; also the names and numbers of the pages that were requested by a specific person and the type of browser he/she uses as well as the date and time of each in-site traffic with a professional search engine to control that information.
13- Security Clearance System for the Control Panel
The system of security clearance provides safe protection for the Control Panel of the system or the website, as more than 60% of breaches occur due to the lack of security systems, and failure to have it simplifies the hacking of the site or system through:
A) Stealing passwords by using key logger software.
B) Use password guessing software to steal login information.
Through the first method, the hacker sends an email containing a link or a picture to one of the site's supervisors, this mail will spy on the personal account and steal the login information for the site or system and send it to the hacker without the knowledge of the supervisors. This way the hacker gets the secret information and the site or System can be hacked in seconds.
The second method used in hacking is the use of password guessing software. The hacker uses one of the passwords guessing programs on the site control panel. Once the correct password is reached, the site is fully hacked. These programs are available online free of charge. By implementing the security clearance system attached to the secure gate service, the two above ways are completely blocked, and the control panel is protected.
14. Analysis of Arabic and English texts by reading the DNS code
One of the advantages of the secure portal that our company started using is its support for the Arabic language in addition to the English language, where the texts issued and sent to the website can be analyzed to determine the quality and nature of the visitor to the site by analyzing the DNS code and comparing it to a giant database dedicated to this purpose. For example, By typing the word "ISIS" on one of the pages of the site, the secured portal will reject that request before reaching the real server and this means preserving the safety and integrity of the real server and here comes the importance of the secure portal.
15 - Intersection of the IP number with a giant database over 10 years old
The Secure Gateway servers memorize and store IP numbers that have already attempted to hack any government website that passes through the secure portal. These addresses have been saved and archived for more than 10 years and are often fictitious addresses for virtual VPN programs and servers, therefore, any request that comes to a government and host site in the data center the secured portal reveals the visitor's IP number and will be compared to the information from a giant database that is more than 10 years old in fraction of a second; if similar or repeated numbers are detected, the request will be rejected immediately and therefore the real server stay completely safe.
16-DNS hosting service
The basis of the work of the website and its transmission on the Internet is the addresses of the DNS. The work of these names is related to the addresses of the IP numbers provided to them, and often the government authorities have the problem of not opening the website due to the incompatibility of the IP numbers of Internet companies in Iraq. And therefore many beneficiary complain of the sites not working or stopped working at all, But the real reason is that the Internet system used does not correspond to the server running the website, and through the secure portal this problem is fully resolved where the hosting of DNS addresses are hosted on the servers of the Secure Gateway, whose IP numbers are neutral numbers and acknowledged globally and therefore then website can be opened by any Internet system.
17 - CDN Service to increase the speed of the system and the website more than three times of the real speed
The CDN service is the acronym of the Content Delivery Network, which means that the files will not be in a specific location but distributed on several servers of the Secure Gateway and these servers are spread around the world.
This technology has a huge benefit, the most important:
A) The speed of opening files and pages of the site, because the files will not be in one server, but in several servers spread around the world and if the visitor is to open the site from a foreign country for example "France", all images and files will open from the nearest server to the visitor and the uploading will be distributed over several servers, which will increase the speed of opening the site.
B) high security in the use of this technology, when the hacker start trying an attack on one of the sites, he/she must hack all servers at the same time for the purpose of changing the contents and this is almost impossible, while in the absence of this technique, the hacker attacks only one server, Click here for an illustration of this technique.
18 - Provide a Load Balance service for sites with high traffic
Often, popular systems and web sites suffer from downtime in the event they receive large numbers of visitors at the same time, for example, in the case of the deployment of application for employments or important news, which attracts a large segment of visitors, the hosting of the regular server does not bear the large load and increasing the server capacity or the size of the Bandwidth does not solve this problem, which leads to the site stop working. Through the Secure Gateway technology we can provide the service of load balance in order to automatically distribute the load on several servers without the interference of the site administrators. It is possible to subscribe to this technology only when needed, for example, can be subscribed for a week or two only.
19 - Two Factor Authentication Service
One of the hallmarks of the Secure Gateway is the availability of two-factor authentication technology, which is known as two-factor authentication to get into Control Panel or important and private files by checking the identity of the person via the phone number and this is done by sending a random code consisting of 4-6 digits And whenever you enter the control panel, a new code is sent to your phone, and the code is in effect for 120 seconds.
The two-factor authentication process is a new security layer that is added to the system or website in order to prevent anyone from login to your system even in case of password leakage, and therefore this technology protects your system from penetration by using spyware such as KEY Logger or using email phishing technology.

1. Do we need to install or purchase devices for the purpose of using Secure Gateway technology?
A/ No, you do not need anything to implement this technology. This is why it is called Secure Gateway. Because we do everything, all you need is to direct the DNS of your system or website to our company and the technique will completely work. All incoming requests to your system or your website will be analyzed, and only real requests will be directed and the requests that aim to hack and sabotage your website will be isolated.
2. Do I need to change hosting or change my hosting company?
A / No, you can host anywhere or in any company as our technology is compatible with all hosting companies.
3. Where can we benefit from this technology?
A/ You can apply the protection to any system or website of any capacity or size.
4. Are there specific programming languages or is the technology compatible with all the programming languages?
A/ Secure Gateway is compatible with all programming languages.
5. How is the subscription to this service?
A/ Subscription to this service shall be on an annual basis.
6. Do I have to subscribe to all the Secure Gateway services, or can I subscribe to some of them?
A/ You can subscribe to some services as you need it.
7. Is there any difference in the speed of the site in case of the use of Secure Gateway technology?
8. A/ The speed of the site will increase because your host server will receive applications only through the servers of the Secure Gateway and therefore the site will respond to customers better because the Processing server will deal with only one IP number and that is the Secure Gateway servers IP.
8. When I subscribe to the Secure Gateway technology, do all the above services apply to my site?
A/ The number and type of services depends on the type of the plan you subscribe to and also depends on the type of programming used in the system or website.
9- If the system or website is programmed by a programmer or a group of programmers, can the system be protected in this way?
A/ Yes, even if the programmers do not have prior knowledge or know how to fill or close the software gaps, Secure Gateway technology is the solution, because we will prevent the hacker from accessing gaps in your site, and prevent the hacker from running programs that detects gaps on the pages of your site and we also check each file uploaded to the system or the site and we track the movement of the visitor within the pages of the site and in the event of discovering any abnormal attempt we will distance the hacker from your site directly.
